Kerberos SSO
This article explains how to configure authentication to an Exasol database with Kerberos SSO.
Exasol supports single sign-on (SSO) functionality using Kerberos in JDBC and ODBC connections. This allows users to authenticate to Exasol using their Kerberos credentials for a seamless user experience.
To enable Kerberos SSO in Exasol, you must have a keytab file provided by a Kerberos Key Distribution Center (KDC) or by your Active Directory administrator in Windows. The keytab file consists of service principals for Exasol databases and must be uploaded to Exasol using EXAoperation.
To learn how to configure a database user to authenticate with Kerberos, see CREATE USER and ALTER USER.
Enable Kerberos SSO in Exasol
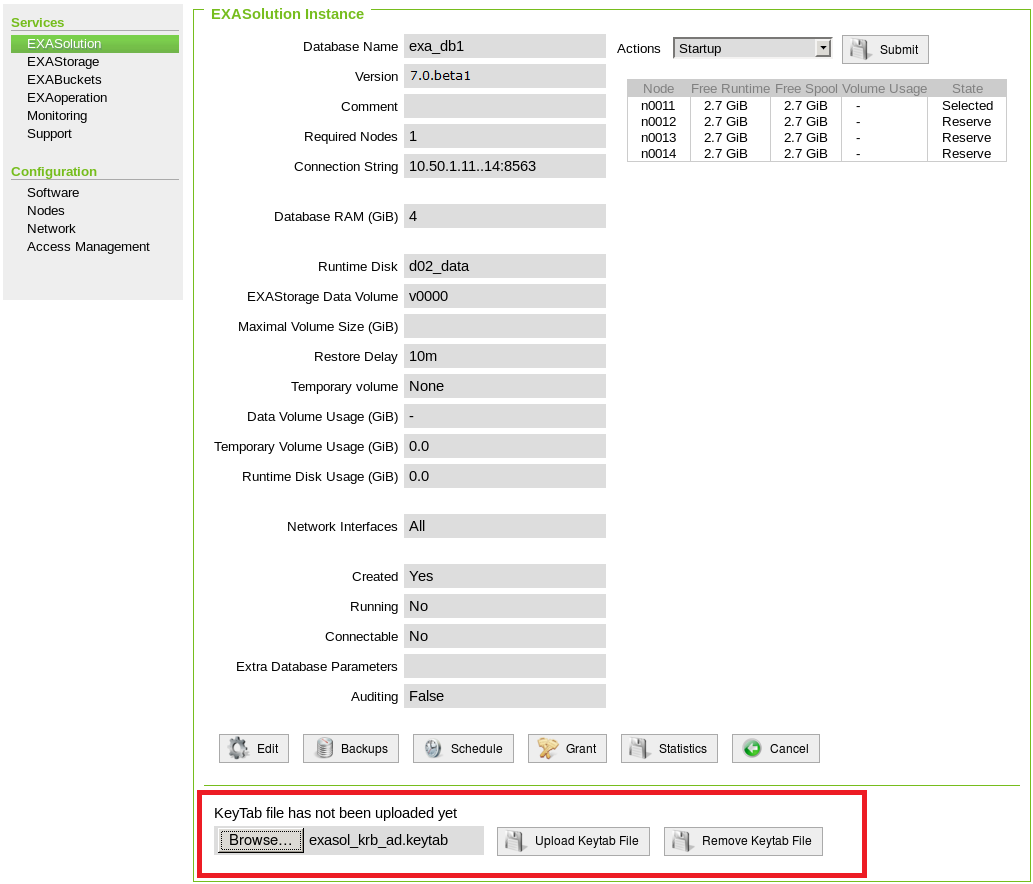
- In EXAoperation, go to Services > EXASolution and select the database name to open EXASolution Instance for it.
- Shut down the database if it is running by selecting Shutdown from the Actions... drop down list and click Submit. Wait until the database is offline.
- Upload the keytab file to be used in the cluster. Click the Browse button located at the bottom and then click Upload Keytab File.
- As an optional step after you have uploaded the keytab file, you can set additional parameter values. Click Edit to edit the database and set the values for the following parameters:
- Kerberos Service Name
- Kerberos Host Name
- Kerberos Realm
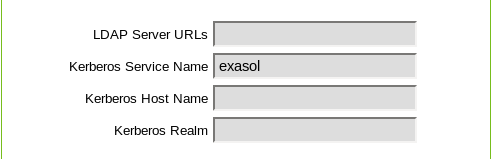
Setting these values are optional. For a brief description of these parameters, refer to the Kerberos Parameters table below.
-
Click Apply and then start the database.
Kerberos parameters
| Parameter | Description |
|---|---|
| Kerberos Service Name |
If a Kerberos Service Name is specified, then only the specified Kerberos service can be requested by the client. If no service name is specified, any Kerberos service requested by the client is accepted provided that the service exists in the uploaded keytab file. The default Kerberos Service Name is exasol. |
| Kerberos Host Name |
If a Kerberos Host Name is specified, then only that hostname is accepted by the client, regardless of whether the uploaded keytab file contains entries for other hostnames. The hostname of the Kerberos principal is valid cluster-wide, which means that it can be considered virtual. If no hostname is specified, the hostname will not be checked during Kerberos authentication. |
| Kerberos Realm |
If a Kerberos realm is specified, then only users of this realm will be accepted, regardless of whether the uploaded keytab contains entries for other realms. If no Kerberos realm is specified, then by default users from all the realms are accepted, provided there is an entry of the realm in the keytab file. |
